Setting up email filters or organizing your emails into folders is an efficient way to manage your emails. To help you organizing your incoming email messages, Windows Live Hotmail can put them in specified folders automatically.You might want to know how to set up email filters to automatically sort your email into folders for better management.
For example, if you want to have a Facebook filter to separate all your notifications emails from your everyday emails. You could also do this for newsletters that you are subscribed to, emails from family members, or emails related to work. As you can see, there are a lot of advantages for filtering your emails.In this blog, I am going to show you how to set up email filters in Gmail and Hotmail .
Creating Filters in Gmail:
The first thing to point out is that Gmail does not use the tradition “˜folder’ structure. Gmail uses “˜labels’, but they are pretty much the same thing, it just has a different name.If you have existing filter then it will be displayed.
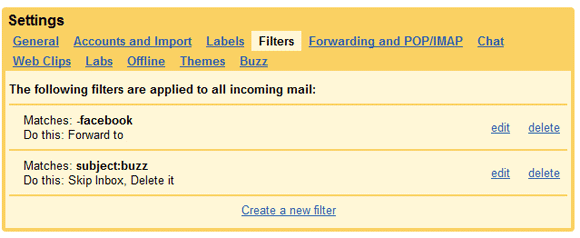
Gmail, Google’s web-based email, is one of the most popular email programs on the Internet. The first thing to point out is that Gmail does not use the tradition “˜folder’ structure. Gmail uses ‘labels’. For create the filter in Gmail follow the given steps:
To: You may have email forwarding or POP access set up on your Gmail account so all your work emails get sent to your personal Gmail account. Therefore, if you want to separate your work emails from personal emails, enter your work email address in the To box. All emails you receive that are sent to the email address you specify, the filter will apply.
Subject: If you enter a phrase in the Subject, any emails with that phrase in the subject would be applied.
Has the words: If the contents of the email has the words you specify, the filter will apply.
Doesn’t have: All emails that do not contain the following phrase you specify, the filter will apply.
Has attachment: All emails with a file attached.

For example, if you want to have a Facebook filter to separate all your notifications emails from your everyday emails. You could also do this for newsletters that you are subscribed to, emails from family members, or emails related to work. As you can see, there are a lot of advantages for filtering your emails.In this blog, I am going to show you how to set up email filters in Gmail and Hotmail .
Creating Filters in Gmail:
The first thing to point out is that Gmail does not use the tradition “˜folder’ structure. Gmail uses “˜labels’, but they are pretty much the same thing, it just has a different name.If you have existing filter then it will be displayed.

Gmail, Google’s web-based email, is one of the most popular email programs on the Internet. The first thing to point out is that Gmail does not use the tradition “˜folder’ structure. Gmail uses ‘labels’. For create the filter in Gmail follow the given steps:
- Logon your Gmail account, to setup an email filter, click on settings which are in the top right corner, then click on Filters.
- To create a filter, click on Create a new filter. Fill the all criteria like…
To: You may have email forwarding or POP access set up on your Gmail account so all your work emails get sent to your personal Gmail account. Therefore, if you want to separate your work emails from personal emails, enter your work email address in the To box. All emails you receive that are sent to the email address you specify, the filter will apply.
Subject: If you enter a phrase in the Subject, any emails with that phrase in the subject would be applied.
Has the words: If the contents of the email has the words you specify, the filter will apply.
Doesn’t have: All emails that do not contain the following phrase you specify, the filter will apply.
Has attachment: All emails with a file attached.

- Click on the “Test Search” button after entering your filter information. You will want to verify that the emails you were trying to filter show up in the test search. If they do not, you will need to tweak the filter options and perform another test search. After confirming that the emails are filtering properly, click on the “Next Step” button.

Create An Email Filter In Hotmail:
- Select Options | More options... (or just Options in Windows Live Hotmail classic) from the toolbar.
- Follow the Automatically sort e-mail into folders link under Customize your mail.
- Click on New filter button.
- Select the desired filtering criterion under Which messages are you looking for?.
- Choose the folder to receive all mail matching your criterion under Where do you want to put these messages?.
- Click Save.