Finally iPhone 5 is out there in our hands, and people are coming up with all of their views and opinion that the much awaited and talked about new gadget has to offer.
The iPhone 5 will surprise you in many ways some of the Top 5 can be the following ways.
The weight
Shaving about an ounce off a phone's heft doesn't sound like a lot, and I've always been skeptical of incremental reductions (20 percent lighter!), but the first thing that shocked me when I picked up the iPhone 5 was how light it was, not how thin it was. There's a reason for this: many smartphones boast large screens and sleek looks, but few weigh as little as 3.95 ounces. Most other iPhones weigh about the same, so it feels different immediately.
The beauty of Maps
Whenever you hear that an app is beautiful to behold, especially an app as integral to the use of the iPhone as Maps, it can't help but feel superfluous. Still, try to look at Maps on an iPhone 5 and not feel wowed. Right now, it's the best graphics demo the iPhone 5 has in its stable, and Flyovers feel intensely surreal, even if you're a Google Earth addict. Whether the graphical finesse of the new Maps and turn-by-turn navigation can make up for the lack of more-refined Google search terms, Street View, and public transit directions feels like a dicey proposition, but Maps is undeniably fun to play with.
The speed
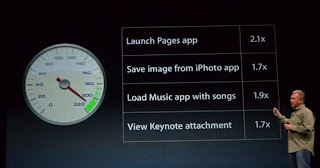 In particular, I'm talking about LTE. I'm not a 4G LTE user at home, and I never thought I'd need it in a phone. Still, the wake-up moment for me was when I opted for FaceTime over LTE instead of Wi-Fi because LTE was more than twice as fast as my home broadband wireless connection, and the connection was smoother. It's a seductive draw: would I end up paying through the nose for LTE for its snappy convenience? I've used it far more than I ever thought I would, at least on the review unit. The A6 processor's harder to appreciate right off the bat, but both combined give this iPhone a serious turbo kick.
In particular, I'm talking about LTE. I'm not a 4G LTE user at home, and I never thought I'd need it in a phone. Still, the wake-up moment for me was when I opted for FaceTime over LTE instead of Wi-Fi because LTE was more than twice as fast as my home broadband wireless connection, and the connection was smoother. It's a seductive draw: would I end up paying through the nose for LTE for its snappy convenience? I've used it far more than I ever thought I would, at least on the review unit. The A6 processor's harder to appreciate right off the bat, but both combined give this iPhone a serious turbo kick.
Lightning doesn't support Thunderbolt
For years, I've wondered when iOS devices would sync via Apple's incredibly fast Thunderbolt port. A new, smaller connector seemed like the ideal opportunity. Then came the name: Lightning. Lightning and Thunderbolt. Yet, the packed-in Lightning cable works via USB. The door could still be open for Thunderbolt (or USB 3.0) in the future. Does faster syncing matter? To me, it does.
Everything changed just a bit
There's no Big Thing on the iPhone 5, but, try to name a part of the phone that hasn't changed. Usually, iPhones keep at least one or two things intact from one year to the next. This year: design, screen, speakers, microphones, cameras, data connection, even connector port and earphones were toyed with. Instead of investing in one game-changer, the iPhone 5's a top-to-bottom tune-up that makes me wonder, just a little bit, what Apple could do to top it next year.
The iPhone 5 will surprise you in many ways some of the Top 5 can be the following ways.
The weight
Shaving about an ounce off a phone's heft doesn't sound like a lot, and I've always been skeptical of incremental reductions (20 percent lighter!), but the first thing that shocked me when I picked up the iPhone 5 was how light it was, not how thin it was. There's a reason for this: many smartphones boast large screens and sleek looks, but few weigh as little as 3.95 ounces. Most other iPhones weigh about the same, so it feels different immediately.
The beauty of Maps
Whenever you hear that an app is beautiful to behold, especially an app as integral to the use of the iPhone as Maps, it can't help but feel superfluous. Still, try to look at Maps on an iPhone 5 and not feel wowed. Right now, it's the best graphics demo the iPhone 5 has in its stable, and Flyovers feel intensely surreal, even if you're a Google Earth addict. Whether the graphical finesse of the new Maps and turn-by-turn navigation can make up for the lack of more-refined Google search terms, Street View, and public transit directions feels like a dicey proposition, but Maps is undeniably fun to play with.
The speed
 In particular, I'm talking about LTE. I'm not a 4G LTE user at home, and I never thought I'd need it in a phone. Still, the wake-up moment for me was when I opted for FaceTime over LTE instead of Wi-Fi because LTE was more than twice as fast as my home broadband wireless connection, and the connection was smoother. It's a seductive draw: would I end up paying through the nose for LTE for its snappy convenience? I've used it far more than I ever thought I would, at least on the review unit. The A6 processor's harder to appreciate right off the bat, but both combined give this iPhone a serious turbo kick.
In particular, I'm talking about LTE. I'm not a 4G LTE user at home, and I never thought I'd need it in a phone. Still, the wake-up moment for me was when I opted for FaceTime over LTE instead of Wi-Fi because LTE was more than twice as fast as my home broadband wireless connection, and the connection was smoother. It's a seductive draw: would I end up paying through the nose for LTE for its snappy convenience? I've used it far more than I ever thought I would, at least on the review unit. The A6 processor's harder to appreciate right off the bat, but both combined give this iPhone a serious turbo kick. Lightning doesn't support Thunderbolt
For years, I've wondered when iOS devices would sync via Apple's incredibly fast Thunderbolt port. A new, smaller connector seemed like the ideal opportunity. Then came the name: Lightning. Lightning and Thunderbolt. Yet, the packed-in Lightning cable works via USB. The door could still be open for Thunderbolt (or USB 3.0) in the future. Does faster syncing matter? To me, it does.
Everything changed just a bit
There's no Big Thing on the iPhone 5, but, try to name a part of the phone that hasn't changed. Usually, iPhones keep at least one or two things intact from one year to the next. This year: design, screen, speakers, microphones, cameras, data connection, even connector port and earphones were toyed with. Instead of investing in one game-changer, the iPhone 5's a top-to-bottom tune-up that makes me wonder, just a little bit, what Apple could do to top it next year.